Account Management
Login Authentication
Login Authentication Persistence Methods
Ensure secure system usage by selecting AWS Cognito or idle session timeout settings based on the environment.
Login authentication persistence methods can be configured in the System Administrator > Application Settings > Login Authentication Persistence Methods menu within the Application environment, not Studio. The screen is configured differently depending on the type as follows.
[AWS Cognito Token Setting Screen] 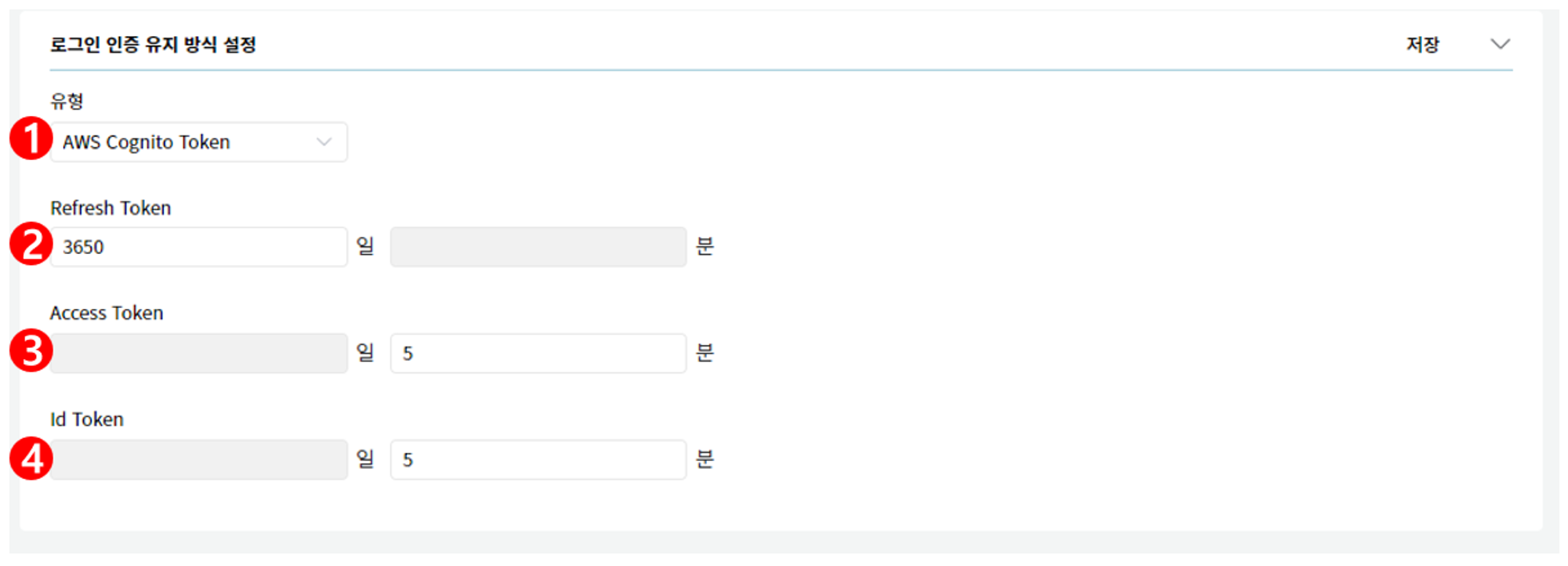
- Type: Area for setting the login authentication persistence method. The default value is AWS Cognito Token, and the controls below are displayed differently depending on the selected type.
- Refresh Token: Area for setting the Refresh Token validity period, which can be between 10 minutes and 10 years.
- Access Token: Area for setting the Access Token validity period, which can be between 5 minutes and 1 day, and cannot be larger than the Refresh Token.
- Id Token: Area for setting the Id Token validity period, which can be between 5 minutes and 1 day, and cannot be larger than the Access Token.
[Client Session Setting Screen] 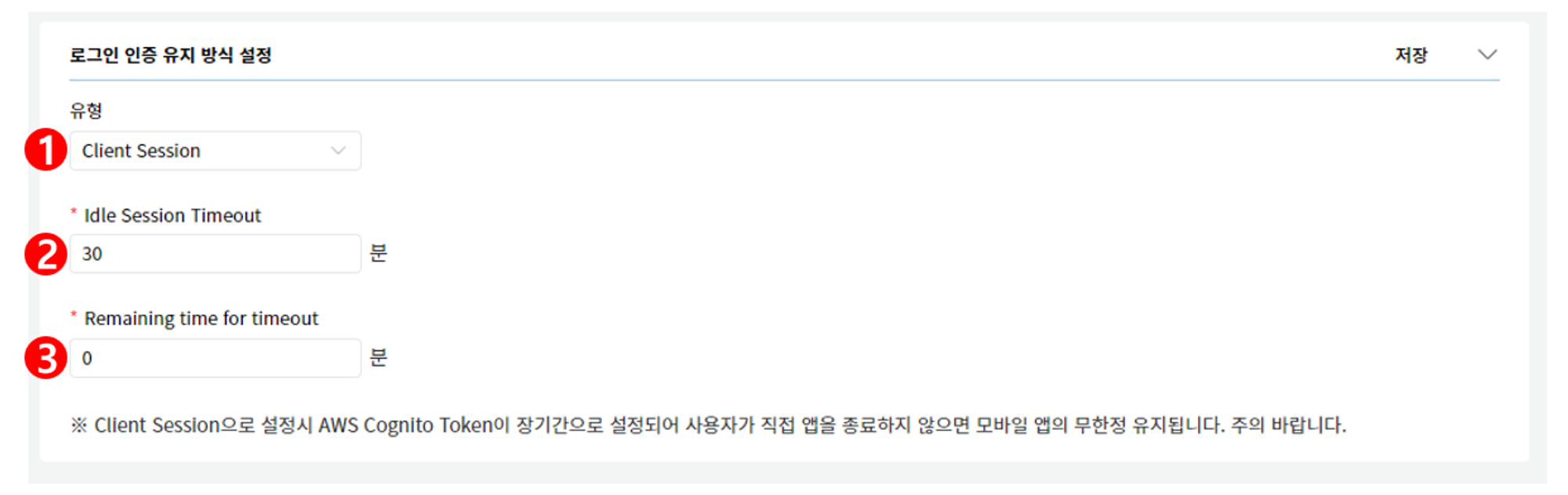
- Type: Area for setting the login authentication persistence method. When changed to Client Session, the Refresh Token is set to 10 years to ensure that the session is not affected by Cognito settings.
Attention
※ Changing to the Client Session method is a feature provided exclusively for the OpenGA Application and cannot be used in other applications.
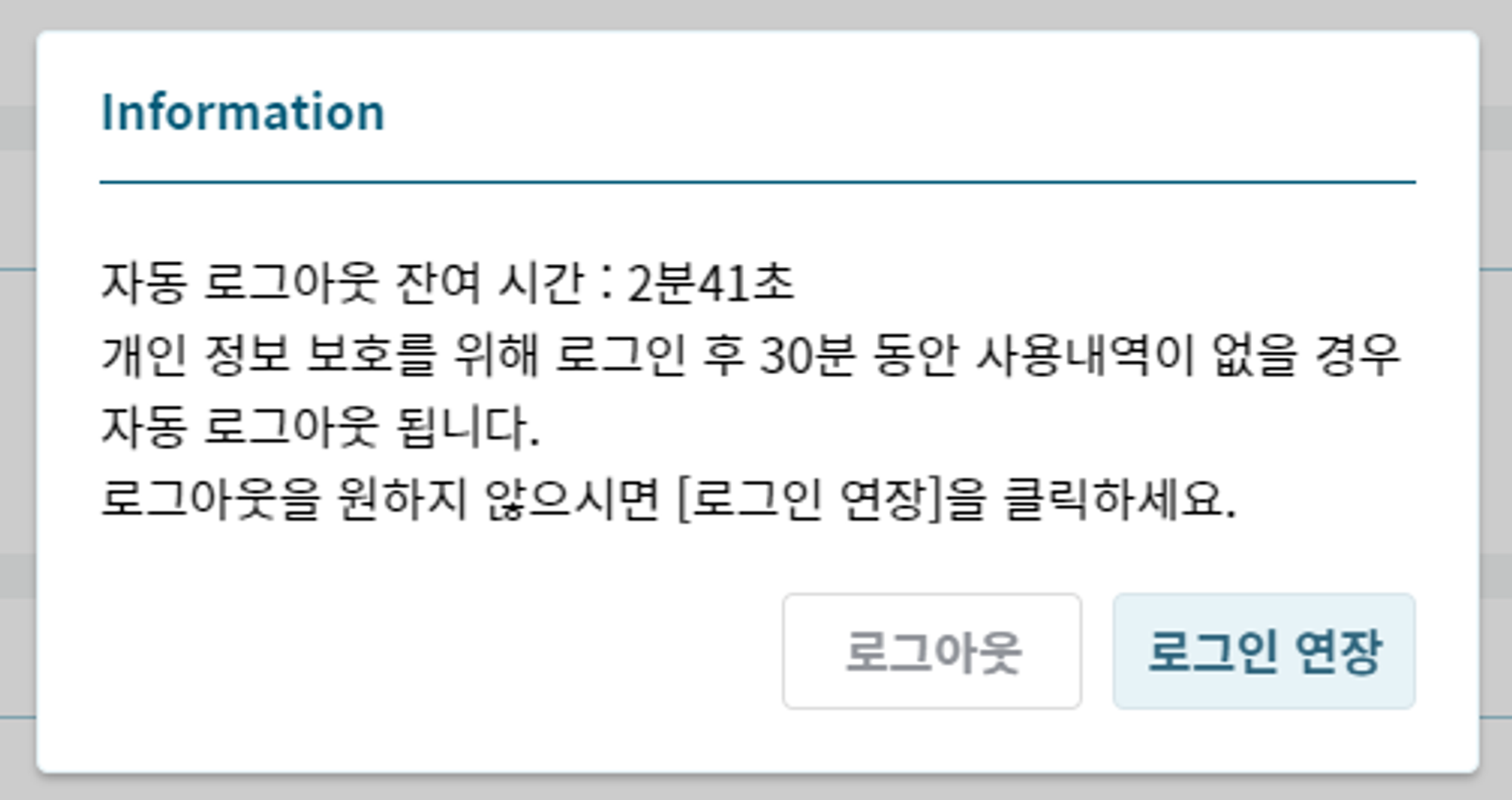
- Idle session timeout: Time after which the user is logged out from the Web Client. For example, entering
120will log out the user if more than 120 minutes have passed since login. - Remaining time for timeout: Time when the login expiration message box is called. For example, entering
5will call the message box 5 minutes before logout, and extending the login from this popup prevents logout.
[Image 3. Logout notification via Message Box when processing login authentication persistence methods as Client Session]